The Jester Hacked?
“The Jester” is a fairly famous opponent of Anonymous; a “Hacktivist for Good.”
Looks like someone has gotten a hold of his Twitter password:
To all my followers, I am sorry. I really am a fraud.: Please forgive me, I did it for the lulz bit.ly/NdPzlI #anonymous #wise
— ʇuıɐs ʞɔopuooq (@th3j35t3r) July 9, 2012
Anonymous: I am sorry for running my mouth all this time. Please spare me. @YourAnonNews @AnonymousIRC bit.ly/OonIxj #anonymous #wise
— ʇuıɐs ʞɔopuooq (@th3j35t3r) July 9, 2012
It’s been fun.: I am in for a LOAD of drama. Next my personal details are unleashed. #wise bit.ly/NBmJdQ #anonymous #wise
— ʇuıɐs ʞɔopuooq (@th3j35t3r) July 9, 2012
Developing…
UPDATE: From a WordPress site devoted to the hack:
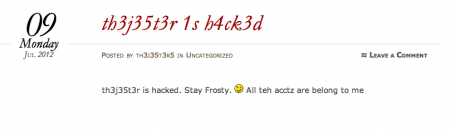
Wow.
UPDATE: Background on the Jester at Wikipedia. It can be edited at any second so it must be reliable! It does, however, provide an interview with the Jester here. An excerpt:
Can you tell us a little bit about yourself and what you do?
Ryan, I would like to give you and your readers a little more about me but it’s kind of difficult to do that, given the nature of my targets, all I can give you sir is what’s already ‘out there’ – I am ex-mil – and slightly pissed at the surge in Jihadist online activities.
Now with regard to what I do: I aim to cause disruption to the online efforts of Jihadists on the internet. They have realized that they can recruit, train and coordinate home-grown terrorists completely via the internet, without ever having to meet. This cuts out much of the risk associated with any face-to-face contact for the recruiters. Web recruitment targets young, tech-savvy, vulnerable Muslims, the iPod generation if you like. By making these sites unreliable, the potential recruit numbers start to dwindle. I limit my hits to defined time-slots (rather than killing them completely) because I am well aware that official Counter Terrorist Agencies use some of these sites for intelligence gathering. I have been asked why I DON’T hit certain sites, well it’s simple. By NOT hitting certain sites (and hitting others hard) I am ‘herding’, people give up easily when a site is constantly up and down, and move on to a more reliable one. So it creates a funnel-effect, funneling terrorists and potential terrorists away from peripheral sites and into a smaller space that is easier to monitor.
There is a fellow named Vince in the Bay on Twitter who claims the Jester wasn’t hacked. Could be. The Jester could be running a scam of some kind. I don’t know. But it ostensibly looks like a hack and so it’s news whether it turns out to be a false flag operation or not.
UPDATE: Vince in the Bay clarifies:
[S]omeone figured out his auto post email that links his wordpress to his twitter.
That may be. But it still looks like a hack of sorts. A lot of messages are appearing on his Twitter account that he didn’t write — that are mocking him. Isn’t that a hack of some kind?
UPDATE: Unclear how Vince in the Bay’s explanation can be reconciled with the claim above that they have control of 14 or so of his online accounts, including Facebook, Twitter, SecondLife, Linkedin, and so forth.
Off to bed. We’ll see what tomorrow brings.

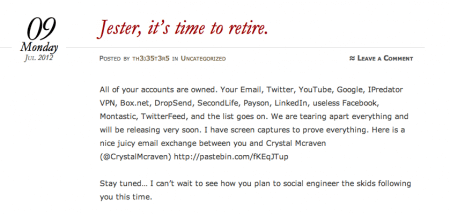


Well, I gotta get to bed. This development kept me up way later than I expected…
Patterico (feda6b) — 7/9/2012 @ 3:03 amVince maybe on to something as i looked at jester twitter page and none of the twits that was on my time line from jester have a look https://twitter.com/th3j35t3r
osiris (978d45) — 7/9/2012 @ 9:45 amThis whole thing is almost like a “Wilderness of Mirrors” but I don’t think it should be that hard to decipher given some careful study and thought.
You have to find out something or things you think are true and work your way from there. Alwsys go first with what has the highest probability of being true.
Of course if you start with (or end up taking as your starting point) the worng idea, like the idea Ron Brynaert is telling the truth, you wind up completely wrong.
Sammy Finkelman (d22d64) — 7/9/2012 @ 9:50 amI think its a false flag, prob tied to his latest project (project looking glass). Wouldn’t be surprised if he sent the tweets and the wordpress site is his -baited to hook people of interest. That along with all the pastebin links…. all bait that his detractors and such might leap at
zerofx (c03bae) — 7/9/2012 @ 9:55 amWikipedia. It can be edited at any second so it must be reliable
You can also almost always check earlier versions, unless the whole article has been deleted maybe.
It is always good to also look at the Wikipedia Talk page, especially on any controversdial or article with disputable facts
http://en.wikipedia.org/wiki/Talk:The_Jester
Articles that has been around for a long time, and/or have engendered a lot of discussion * may have archives talk pages. There are always leads there.
[*] The Shooting of Travon Martin article hasnb’t been around all that long but has many archived talk pages, probably more than Pearl Harbor does now:
http://en.wikipedia.org/wiki/Talk:Shooting_of_Trayvon_Martin
Some things may get deleted from the talk pages but anything that has to do with what the article should say stays.
Wikipedia also sometimes (because so few people in some cases can edit contorversial articles) is behind events.
Sammy Finkelman (d22d64) — 7/9/2012 @ 9:58 amThis is how the jester supposedly spied on people:
(from wikipedia)
On March 5, 2012 The Jester changed his Twitter account @th3j35t3r avatar from his signature Jester icon to a QR Code without comment or explanation.[37] QR Codes are bar codes that can be scanned by mobile phones and are most often used in advertising. Scanning a QR Code redirected the browser to a website.[38]
Scanning The Jester’s icon led to a URL where he had an image of his signature Jester icon and an embedded, hidden code that allegedly exploited a vulnerability that affects Safari, Chrome and Android browsers.[37]
“When anyone scanned the original QR code using an iPhone or Android device, their device would silently make a TCP shell connection back to my remote server,” The Jester wrote. “Like a phone call, if you like.”[37][not in citation given]
Apparently, once connected to the Jester’s server, the network diagnostic tool NetCat checked the connecting mobile device to see if it had Twitter software installed.[37]
Twitter account information was then harvested and checked against a list that The Jester allegedely maintains of known Twitter accounts associated with the hacking groups Anonymous, LulzSec or AntiSec, with Wikileaks, Al Qaeda and Islamic Jihadi recruiting sites.[37] Twitter accounts that did not hit a match to the list were ignored.
Possibly, when a Twitter account registered a hit on the list, the account permissions were transferred to The Jester, he elevated his permissions to allow him to exploit the entire mobile device. It is possible that in this manner The Jester was able to obtain access to SMS text messages, voicemail, call logs, and email on the phone.[39][40]
The Jester’s QR code ran quietly for five days before a Twitter user going by the moniker rootdial noticed the embedded code and mentioned it.[37]
In those five days, The Jester wrote “Over 1,200 curious netizens scanned the QR code . . . Of those, over 500 devices reverse-shelled back to the listening server. Of those, a significant number were on the ‘[hit]-list’ and as such treated as valid targets.”[37][41]
The Talk page says:
[edit] Contradiciton
The text says that the hack was in the web page where the QRcode redirected. The quote to back it up suggests that the QR code directly caused the link to the shell. Rich Farmbrough, 23:18, 21 May 2012 (UTC).
A QR only goes to a web page I think. So this was a web page that loaded and ran a program?
Sammy Finkelman (d22d64) — 7/9/2012 @ 10:05 amSounds like criminal hacking.
spointer (398361) — 7/9/2012 @ 10:34 amDepends on the QR code application and the device. Some devices allow the codes to launch arbitrary applications, which is apparently what he used.
Rob Crawford (04f50f) — 7/9/2012 @ 2:04 pmI am a hardworking professional conservative. As such, I party, debate issues and read news voraciously, especially sites like Patterico’s. Yet, I never comment. I’m prompted to comment on this story because I have to say, I’ve never in all my years read the writings of anyone as genius as The Jester. He’s entertaining, brilliant, and one of the good guys.
For those who don’t know, read about him. He takes down asshole geniuses by outsmarting them.
Learn.
JP (cc5afb) — 7/10/2012 @ 12:50 amhttp://th3j35t3r.wordpress.com/2012/07/10/rumors-of-my-untimely-early-retirement-are-greatly-exaggerated/?utm_source=Jesters+Court+Blog&utm_medium=twitter
MCreamer (5a8fb9) — 7/10/2012 @ 8:29 pm